One of the main goals of the NFDI Section Common Infrastructures is to create a multi-cloud-based basic infrastructure that enables unified access to data, software, and computing resources, as well as sovereign data exchange and collaborative work. To achieve this goal, existing and emerging Identity & Access Management (IAM) systems must be interconnected and extended in such a way that researchers from different fields and institutions can access NFDI resources as easily yet securely as possible. Interoperability is therefore a key requirement, not only within the NFDI, but also in terms of access to and exchange with external infrastructures such as the European Open Science Cloud (EOSC), National High Performance Computing (NHR), and the Gaia-X ecosystem. To manage the complex relationships between identity sources, virtual organizations, access management solutions, and each type of resource, a decentralized, federated identity and access management is required.
The technical and organizational framework for a federated IAM is a so-called authentication and authorization infrastructure (AAI). An AAI is traditionally implemented within the framework of national identity federations, which are usually operated by the respective national research and education networks (NRENs). NRENs customarily act not only as generic infrastructure providers, but also as “trust anchors” in particular. The German NREN DFN has been operating the national identity federation DFN-AAI, one of the largest federations worldwide, since 2007. Through its modular architecture and participation in the international interfederation service eduGAIN, DFN-AAI enables international, cross-federation and cross-community usage scenarios. Other identity providers (IdPs) with a different level of trust are social sign on systems, e.g. ORCiD. Regarding AAIs for research communities, the AARC Blueprint Architecture (AARC BPA) has become a best practice solution in several research communities and projects in recent years. Following this pattern, community AAIs operated by one or more research infrastructures connect to an existing national identity federation through a well-defined interface, an SP-IdP proxy, which acts as a service provider (SP) vis-à-vis the identity providers (IdPs) of the home organizations registered in the national identity federation participating in eduGAIN (see Figure 1).
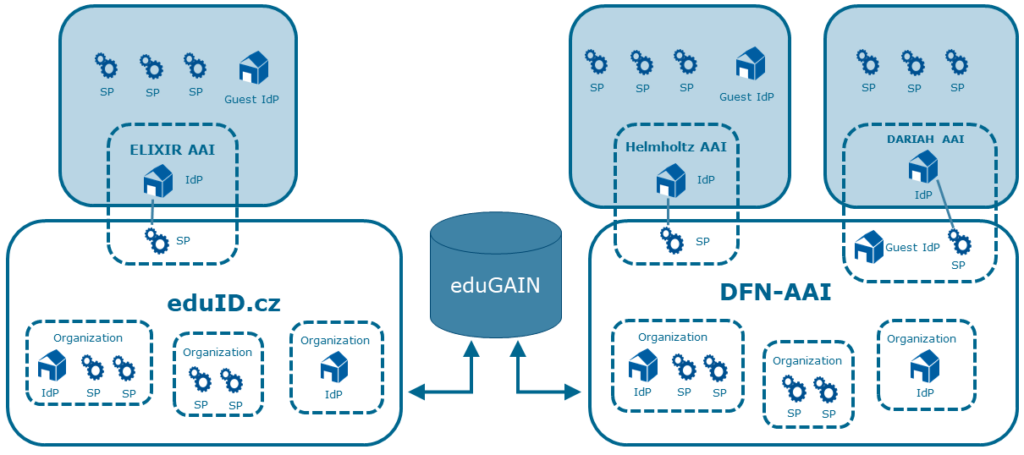
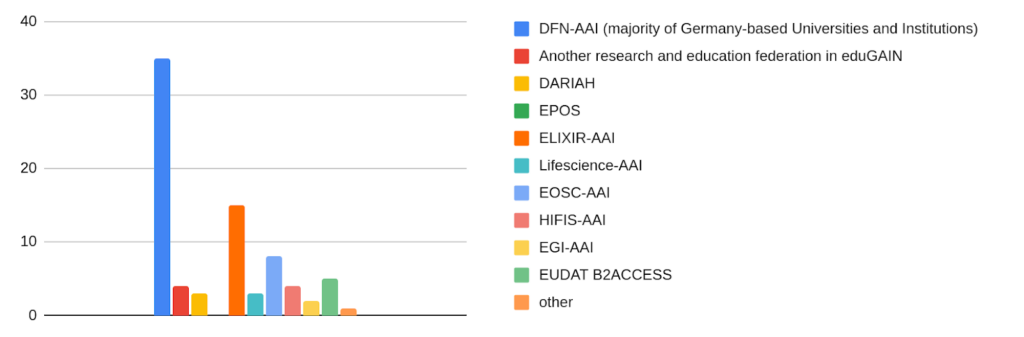
To address the highly decentralized AAI landscape used in the NFDI, together with the “Task Force Tools AAI” we conducted a survey among the NFDI consortia of the first, second and third round of funding. We collected responses from 40 services in 15 NFDI consortia. The orientation towards the existing, federated DFN-AAI is clear. Alongside these are some community AAIs, such as ELIXIR-AAI, which combine national federations into a kind of meta-federation and add further functionalities such as virtual organization management. Figure 2 shows the spread of AAIs within the current services offered by the different NFDI consortia.
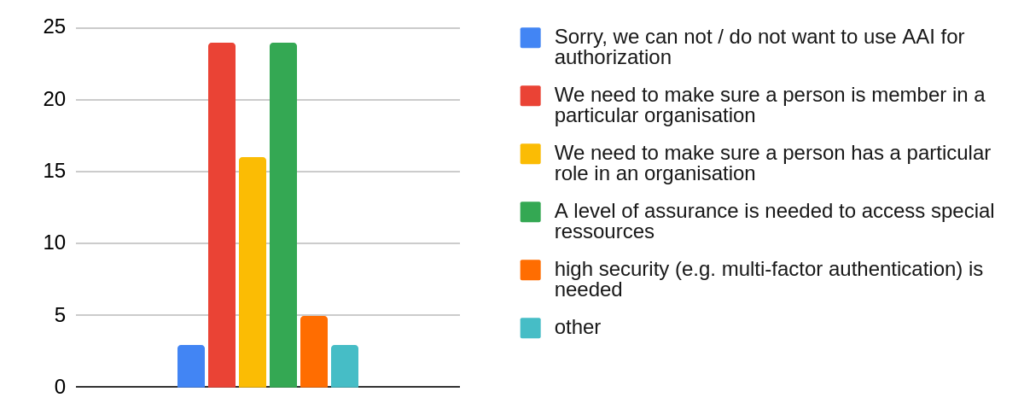
In addition to authenticating individuals, AAIs provide an identity management framework to transmit further information, so-called attributes, about the authenticated identities to the services. Examples include membership in (formal or virtual) organizations or organizational units (e.g. “member of the group of employees at RWTH Aachen University”), roles within organizations (e.g. “person responsible for data management at the Institute of Surface Technology”), or reliability classes (levels of assurance) of identities (e.g. “identity has been confirmed by credential verification”). Figure 3 shows the requirements for AAIs from the perspective of the services offered by the NFDI consortia.
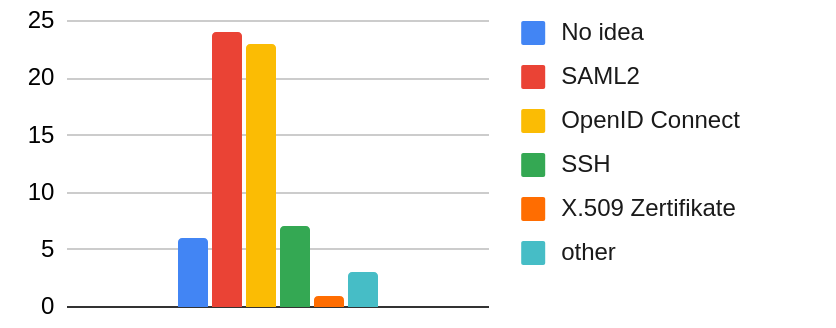
On the technical side, authentication can be performed using various protocols. Two approaches are clearly dominant within the NFDI: SAML2 and OpenID Connect (OIDC). Figure 4 shows the required protocols for authentication within the services offered by the NFDI consortia.
It should be noted here that the existing Identity Federations communicate via SAML2 and a translation to OIDC is usually performed by so-called “Token Translation Services”. This procedure is compatible with the existing AARC BPA. Now that we compiled an overview of the existing frameworks for authentication, the next step will be to incorporate the knowledge gained into the coordination processes within the NFDI and thus ensure that future developments take into account connectivity with the frameworks specified by Gaia-X. |
Within the NFDI, a working group “Identity & Access Management” is currently being formed to clarify the interfaces, especially within the “Common Infrastructures” section. The working group will play a key role in the compilation and technological development. The findings of the FAIR Data Spaces project will be directly incorporated into the working group. A central goal of the working group is to work towards providing an AAI as a basic service through which the NFDI consortia can be centrally connected. Such a node could then also facilitate the link to the Gaia-X infrastructure.
Marius Politze together with Task Force Tools AAI